Article Analysis
Each article's goal is to inform the reader about Meltdown. However, the focus is different. Tech Crunch's focus is on making the topic digestable to the common person. They don't use words that would only be understood by computer scientists. Instead, they make sure the reader understands that the problem affects almost every computer regardless of OS and they give some insights into how the problem may affect the readers' lives. By contrast, the scholarly paper provides a microscope into how the vulnerability occurs, how to reproduce it, and how it can be used on any OS and all 3 big CPU brands. There is enough detail so that anyone with the knowledge can reproduce the Meltdown vulnerability.
TechCrunch
With Tech Crunch's audience being much larger and less educated in computer security, the information given by the article can be entirely found in the abstract and introduction of the scholarly paper. The article has a Q&A format for readers to easily parse what they want to know. Tech Crunch also provides a lot of information about how the world will be affected. They make sure the reader understands that tech companies are working hard on a fix, but a good fix hasn't been found yet. They also give reason to the question about why the authors of the scholarly paper waited seven months to tell the public. Overall, the Tech Crunch article did a great job at informing the reader about questions they may have, even if they read the scholarly paper.
That being said, the article did make false claims. Tech Crunch claims Meltdown is "able to see and modify [data] at will"[2] even though the Meltdown scholarly paper never makes this claim. Meltdown is only able to read data. The Spectre vulnerability, also discussed in the TechCrunch article, is able to modify data so the author may have confused the two. This factual error is small for the average reader, but it displays how Tech Crunch is not as factually thorough as a peer reviewed paper.
Meltdown Scholarly Paper
The audience for the scholarly paper is computer scientists that specialize in low level security. This audience is small, but a large portion of the audience will use the information in their profession. Engineers at Intel and AMD for intance have been using this article for the last seven months to figure out how to implement the best fix, similar to the solultion given in the article. The article makes use of images for diagrams of the CPU's architecture and even has raw bit output of the memory that the authors were able to hack as shown in the image below.
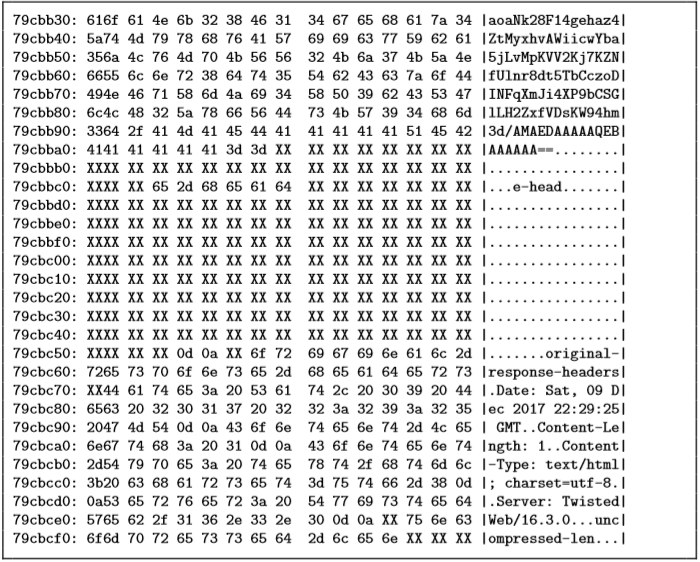
The rehtoric used is extremely dense, also. For each section of the paper, if a reader were to glaze over a single line, they would be forced to go back and re-read. Otherwise the rest of the section will probably not make much sense.
A large number of words that only computer scientists would understand are included in this paper, also. Acronyms like "KAISER", "RAW", "CDB", and concepts like "out-of-order execution"[1] are used frequently with little to no explanation. Several diagrams are offered, however, which helps a lot with the explaination. TechCrunch's article only displays the Meltdown logo and no diagrams, but again that article is not designed to explain Meltdown, just it's effects.
Article Analysis
Each article's goal is to inform the reader about Meltdown. However, the focus is different.
Continue readingForum Analysis
Tech Crunch is known for being a leader in tech pop culture. They are often the go-to place for new and possibly impactful news.
Continue reading